Identity And Access Management Architecture Diagram
The shifting of users applications and management to the cloud and the acceleration of it innovation has forever altered the iam landscape. Identity and access management systems not only identify authenticate and authorize individuals who will be utilizing it resources but also the hardware and applications employees need to access.
 Use Cases Federal Identity Credential And Access
Use Cases Federal Identity Credential And Access
Getting started with identity and access management for mobile security p a g e 4 2 mobile application security with ibm security solutions it is important to understand the various touch points of a mobile security engagement in your system architecture.
Identity and access management architecture diagram. 13 october 2016 analysts. 2017 planning guide for identity and access management. Identity and access management presentation uniting identity and access management identity and access management are tightly coupled by the governance and consumption of identity data.
The visitor management system and federated access manager are both important components to grant access to external system users. Integrated identity and access management architectural patterns 3 there are several common specific business requirements that organizations can address through an iam solution. Mackey explores the essentials of identity and access management from the role of directories to effectively establishing approval workflows.
Microsoft architecture for identity access management iam part 2 federation federation has become one of many standards applied to single sign on sso by organizations. The first identity and access management iam system at northwestern was developed internally in 1993 to save labor in establishing email accounts and to support authentication through the universitys modem pools. Applications platforms authentication authorization workflow application integration resources id sources employees customers business partners users human resources contractor s.
Youll walk away with tips for tackling the five key challenges in managing identities and effective access control strategies. Identity and access management the growing number of web enabled applications and the changing roles of different user communities creates challenges for the modern enterprise. Identity management also known as identity and access management is a framework of policies and technologies for ensuring that the proper people in an enterprise have the appropriate access to technology resources.
Identity management and identity and access management or iam are terms that are used interchangeably under the title of identity management. The access management tool helps to execute run time authentication and authorization decisions leveraging the workflow tool to gather pertinent information from the other icam systems. The evolution of iam at northwestern.
This would include locally hosted claims aware applicati. Mark diodati homan farahmand paul rabinovich lori robinson mary ruddy erik wahlstrom. Provide a method of provisioning and de provisioning of user accounts across the organization using the approval processes established by the business.
How to build an identity and access management architecture. The changing context for iam. Idm systems fall under the overarching umbrella of it security and data management.
The credential management system contains management software that processes sponsored requests for credential registration creates issues and. Figure 1 ibm mobile security and management framework outlines the various.
 Architecture Wso2 Identity Server 5 X X Wso2 Documentation
Architecture Wso2 Identity Server 5 X X Wso2 Documentation
 Privileged Access Management Pam Solutions Ekran System
Privileged Access Management Pam Solutions Ekran System
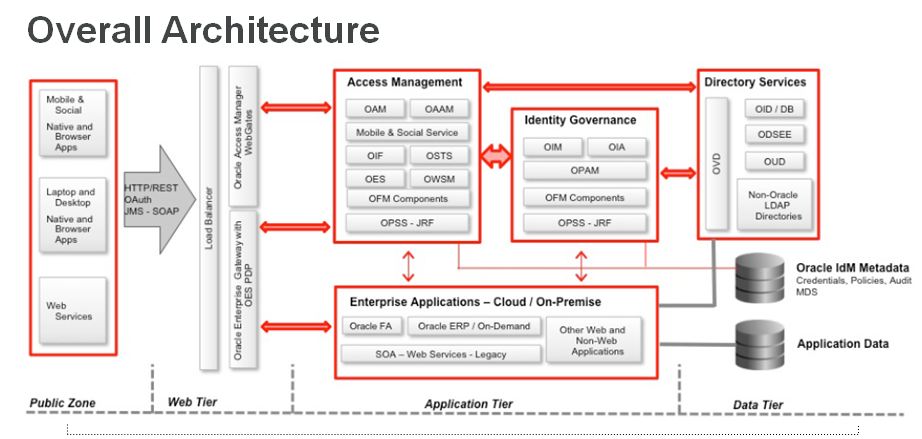 Ayts Summary Of Access Management Session Amis Oracle And
Ayts Summary Of Access Management Session Amis Oracle And
 Azure Appfabric Access Control Service Acs V 2 0 High
Azure Appfabric Access Control Service Acs V 2 0 High
 End To End Security Management For The Iot Ericsson
End To End Security Management For The Iot Ericsson
A Solution To Sso Authentication And Identity Management
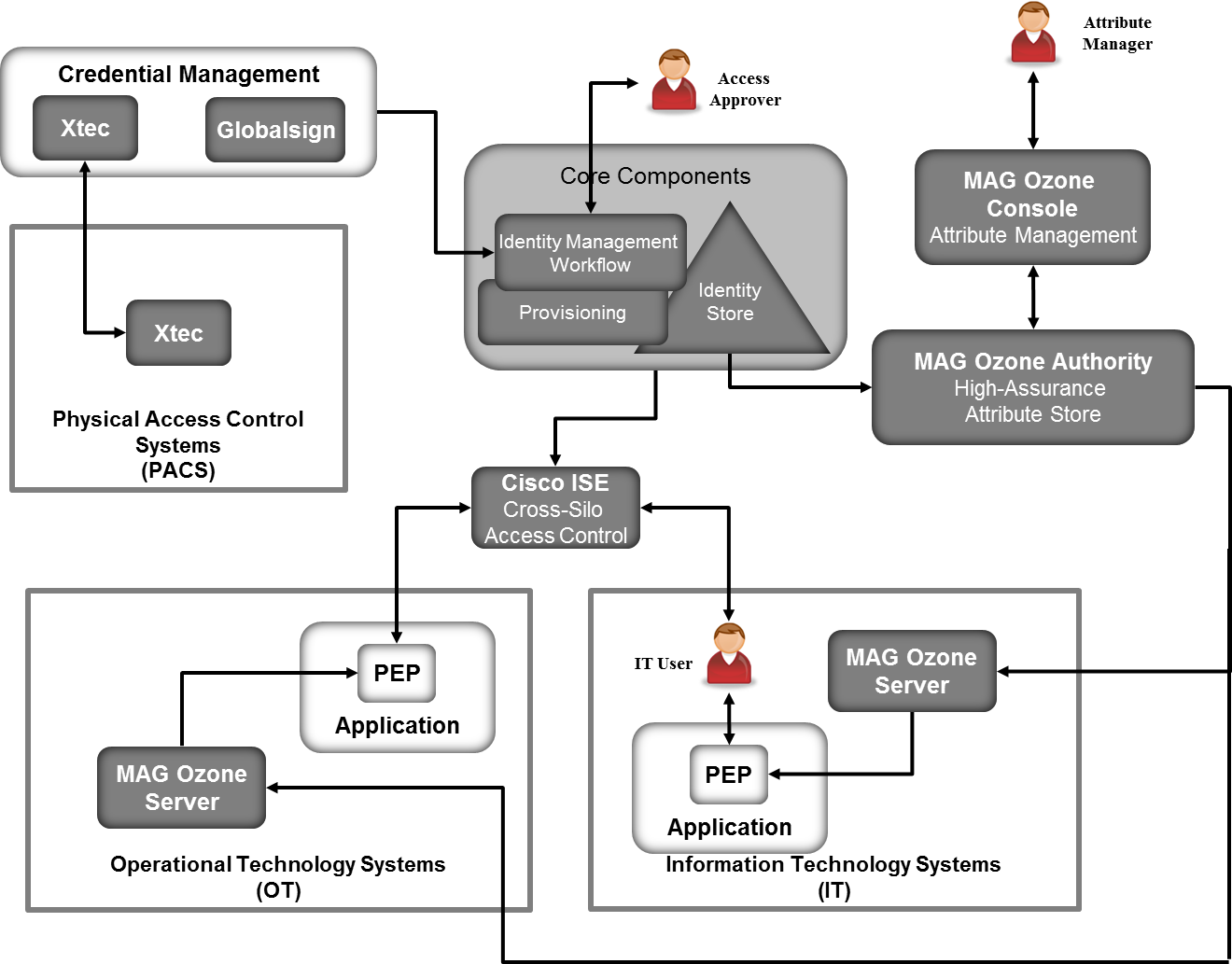 Identity And Access Management Nist Sp 1800 2
Identity And Access Management Nist Sp 1800 2
Energy Sector Identity And Access Management Es Idam Build
Web Access Management Application And Database Security For
Salesforce Certified Identity And Access Management Designer
 Conceptual Architecture Implementing Microsoft Dynamics
Conceptual Architecture Implementing Microsoft Dynamics
 Identity And Access Management Health Check
Identity And Access Management Health Check
Security Identity Access Management Realtek Llc
 What Is Federated Identity Management
What Is Federated Identity Management
 Basic Architecture Of Identity And Access Management Systems
Basic Architecture Of Identity And Access Management Systems
Salesforce Memo How To Prepare For And Pass Identity And
Universal Access Management Uam I Sprint Innovations
 Microsoft Architecture For Identity Access Management Iam
Microsoft Architecture For Identity Access Management Iam
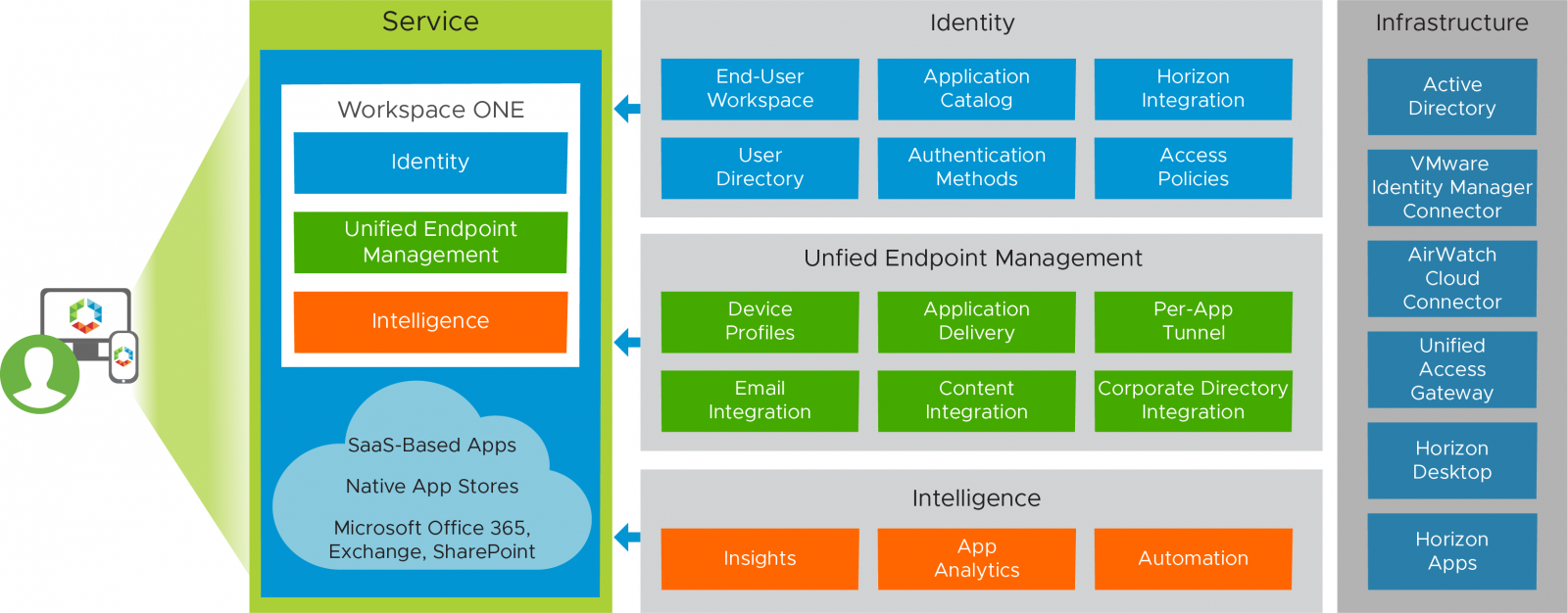 Vmware Workspace One And Vmware Horizon Reference
Vmware Workspace One And Vmware Horizon Reference
 Simplifying Identity And Access Management Of Your Employees
Simplifying Identity And Access Management Of Your Employees
 An Introduction To Tier Reference Architecture Internet2 Blogs
An Introduction To Tier Reference Architecture Internet2 Blogs
 Introduction Federal Identity Credential And Access
Introduction Federal Identity Credential And Access

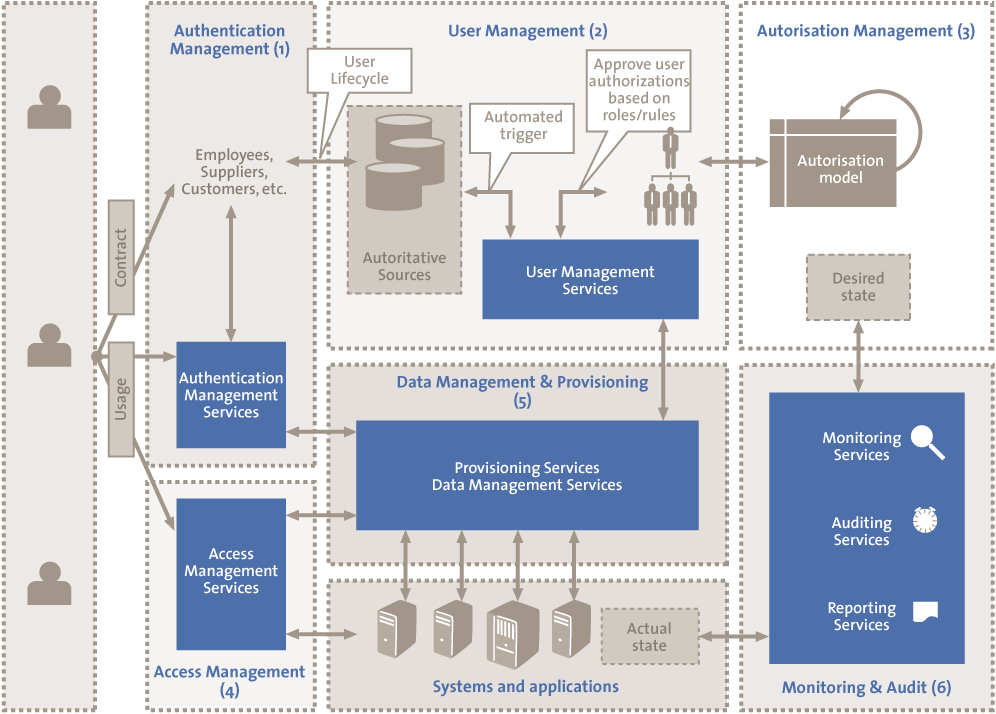

Belum ada Komentar untuk "Identity And Access Management Architecture Diagram"
Posting Komentar